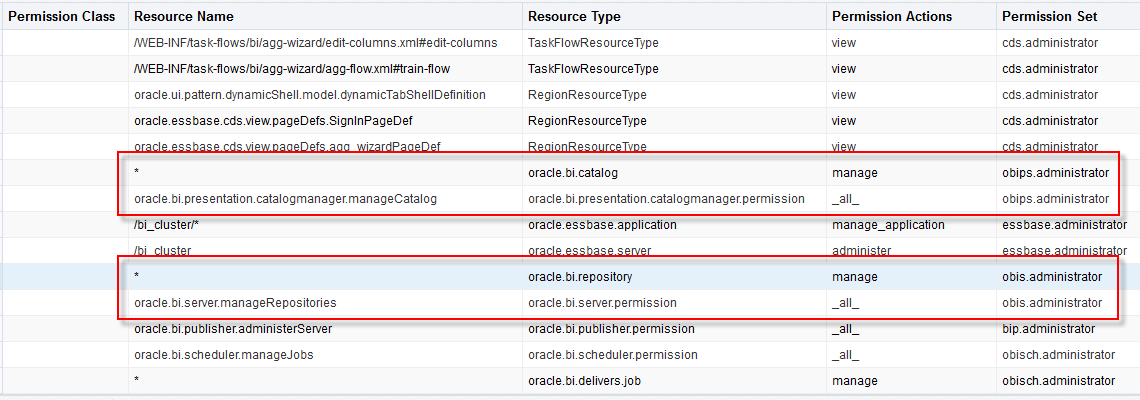
With last Friday’s release of Oracle Analytics Server and Gianni beating just about everybody to a first write-up on how to get it running (after getting the correct versions first) I thought it would be time for a real-world reality check of this newest incarnation of the Oracle Analytics family for on-premises clients.
OAS it the gateway to OAC with pretty much seamless moving from OAS to OAC or deploying things both on-premises and in-cloud in a hybrid setup. New features galore but in turn a dependency on assuring that on-premises is built in a way that they can be moved to the cloud easily. More on this in a moment.
This release is aimed at lifting existing OBIEE customers on par with OAC in terms of functionalities. Customers who for whatever reason do not want or can not move to the cloud. A decision which is valid in and of itself as not everything or everybody has to go to the cloud.
Many functionalities of OAS which weren’t available on-premises so far at all and/or were tied to additional licensing costs are given to customers with existing licenses – for free. Now I have to say it fulfills this bit more than well. To say that Oracle was generous in scooping ladles of additional stuff into it is an understatement.
You can see a full list off features differences here.
However….
HOWEVER the huge issue I see is precisely that list of feature differences combined with the fact that most OBIEE customers have systems that are running since years, are very mature, HIGHLY integrated into their other business-critical systems and their business processes. You know…the things companies actually use to make money. Sadly almost all existing things that aren’t fancy eye-candy for executives but make a solution successful and workable are marked as “deprecated” which translates to:
“Deprecated: Deprecated features won’t be enhanced in the future but are supported for the full life of the Oracle Analytics Server 5.5.x release. Where indicated, a deprecated feature might be desupported in a future, major release. “
- Oracle Marketing Segmentation – Well isn’t that a major punch below the belt line. Using analytics as the marketing engine for Siebel was half the reason Siebel bought nQuire in the first place. Getting rid of said segmentation engine for Siebel Marketing and drop the related functionality may cause existing customers to both leave both Analytics and Siebel. One stone, two birds. Sadly not the good kind of kill.
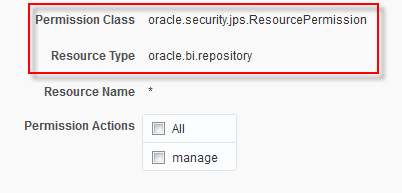
- Flat Files and XML-based Data Sources – Having this in DV is fine, but confining its use to data sets and no longer have the ability to model it properly into corporate data structures? A step back since you simply do not have the same level of integration and access control in terms of detailed row-level filtering and even attribute filtering/masking anymore.
- Session Personalization using System Session Variables – Now this is just silly. It seems that nobody ever went through any RPD of clients with thousands of users in worldwide implementations and went “Oh hey they are actually using this to make the system react more dynamically without hard-coding 5 gazillion things!”.
- Act As Another User – Again how can anybody who worked more than 2 weeks on any real life project consider this a candidate to be deprecated? Ever had to Act As another user around the globe to see his data or pick up his slack or troubleshoot? Can you imagine that not every business user is ok with planning a meeting to screen-share with you because they have more important things to do like running the business? Thought not.
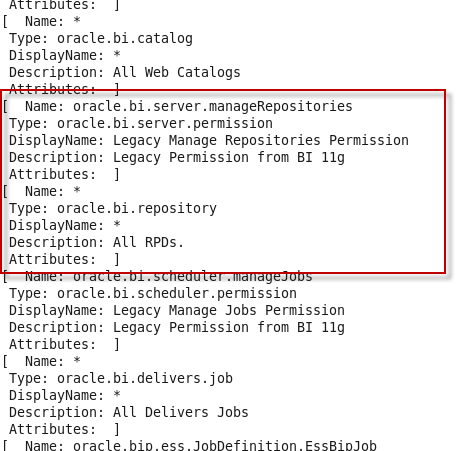
- Database Storage for User Group Memberships – The absolute kicker. This takes the cake (with cream and cherry on top). Like deprecating Marketing Segmentation but taken to the extreme. Customers using other Oracle applications and leveraging what they have already implemented there to help secure and control analytics from a functional, content and data access control perspective are being left out in the cold.
I love OAC and what it has done to the product line and brought to the cloud line-up. But OAS? With that feature list? Well I only hope somebody realizes that it may not be a good idea to completely disregard the existing and blindly chase after buzzwords when compiling the list of things to remain in the product.
Bet on the future and continue developing things in that direction but please don’t sacrifice the existing things on the altar of the new. Especially if the reason is just “because reasons”.